
Remember the 5Ws? Let’s Zoom In.
In my last post, we introduced a timeless tactic — the 5W Strategy — to give structure to cyber investigations.
Now we’re digging deeper into the most exciting W of them all: Who.
Who broke in? Who wrote the malware? Who ghosted your firewall like it owed them money?
It’s time to get personal with threat actors.
Who Did It? Threat Actor Identification
Not all cyber crooks wear hoodies—but they all leave clues. Sometimes you’ll know them by name (APT29), sometimes by motive (financial), and sometimes just by their vibe (super sus traffic at 2:47AM).
Types of Threat Actors
| Category | Motivation | Examples |
|---|---|---|
| Nation-State | Espionage, influence, disruption | APT29 (Cozy Bear), Lazarus |
| Cyber-criminals | Financial gain | FIN7, LockBit, Clop |
| Hacktivists | Ideological activism | Anonymous, Killnet |
| Insiders | Revenge, negligence, profit | Rogue admins, angry ex-staff |
| Script Kiddies | Clout-chasing, curiosity | Low-skill opportunists |
Attribution Sources
- OSINT: Dark web chatter, GitHub scripts, forums
- MITRE ATT&CK for known TTPs
- Vendor Reports: CrowdStrike, Mandiant, Recorded Future to name a few
If you’re blaming North Korea or Russia for every ransomware hit, you might need to re-calibrate your radar. Attribution is science, not guesswork.
What Have They Been Doing? (Known TTPs)
TTPs — Tactics, Techniques, and Procedures — are like threat actor signatures. When you see them in the wild, it’s like recognizing a burglar by their crowbar and crow tracks.
Example TTP Table
| Group | Initial Access | Privilege Escalation | Command & Control | Exfiltration Method |
|---|---|---|---|---|
| APT29 | Phishing, MFA bypass | Credential dumping | DNS tunneling, HTTPS | Encrypted ZIP to cloud |
| FIN7 | Malicious attachments | PowerShell abuse | Custom backdoors | SFTP, Dropbox API |
| Conti | RDP brute force | Admin tool hijacking | Cobalt Strike | RAR over HTTP |
Use MITRE ATT&CK Navigator to track and visualize these techniques.
What did they do in your Org (Internal Threat Intelligence)
Now we cross-reference public intel with what actually happened inside your network.
Common Signs of Actor Activity:
- New accounts created after hours
- Beaconing traffic to suspicious domains
- Files staged in temp folders before exfil
- Lateral movement using legitimate tools (LOLbins)
Simple Real-World Parallel:
Imagine your house gets broken into. You notice muddy footprints, a missing TV, and a half-eaten cookie. From that, you figure out if it’s a hungry burglar, a teenager, or maybe Santa on the wrong day.
What Could They Do Next? (Threat Forecasting)
Threat intelligence is predictive. Based on past patterns, what might this actor do next?
Threat Forecasting Template:
| If Actor Did… | They Might Next… |
|---|---|
| Dumped credentials | Move to cloud apps or VPN abuse |
| Gained domain admin | Deploy ransomware or wipe backups |
| Exfiltrated R&D files | Sell IP or use for spear phishing campaigns |
Bonus Tip: Map their likely goals to Crown Jewels in your org (e.g., customer data, financial systems, trade secrets).
How Do You Prepare? (Threat Actor Playbook)
Every known actor should trigger a playbook that includes detection, response, and business alignment. Each threat actor deserves their own “Oh no, not again” playbook.
| Stage | Response |
|---|---|
| Phishing emails | Block sender domains, scan attachments in sandbox, alert users with awareness prompts |
| Known malware | Add indicators to EDR/AV tools, isolate affected systems, initiate memory analysis |
| Beaconing C2 | Block outbound traffic to suspicious IPs or domains, enable proxy inspection |
| Data exfil signs | Trigger DLP alerts, investigate traffic patterns, notify legal/compliance teams |
Example: Mini Playbook for LockBit Ransomware
- Detection: Unusual PowerShell execution combined with volume shadow copy deletions.
- Containment: Immediate EDR quarantine of affected systems, revoke compromised credentials.
- Eradication: Deploy scripts to remove known malware artifacts and scheduled tasks.
- Recovery: Restore from verified backups, rotate all admin passwords.
- Post-Incident: Conduct root cause analysis, review playbook effectiveness, brief leadership.
Looking for real playbooks? Check out TheHive Project and Sigma Rules.
The INTELscope Pyramid: From TTP to Boardroom
From the nitty-gritty (TTPs) to boardroom-level “why does this matter,” this model helps security leaders show value across layers of defense and strategy. Here’s the full strategy pyramid that connects technical threat detection to executive risk strategy.
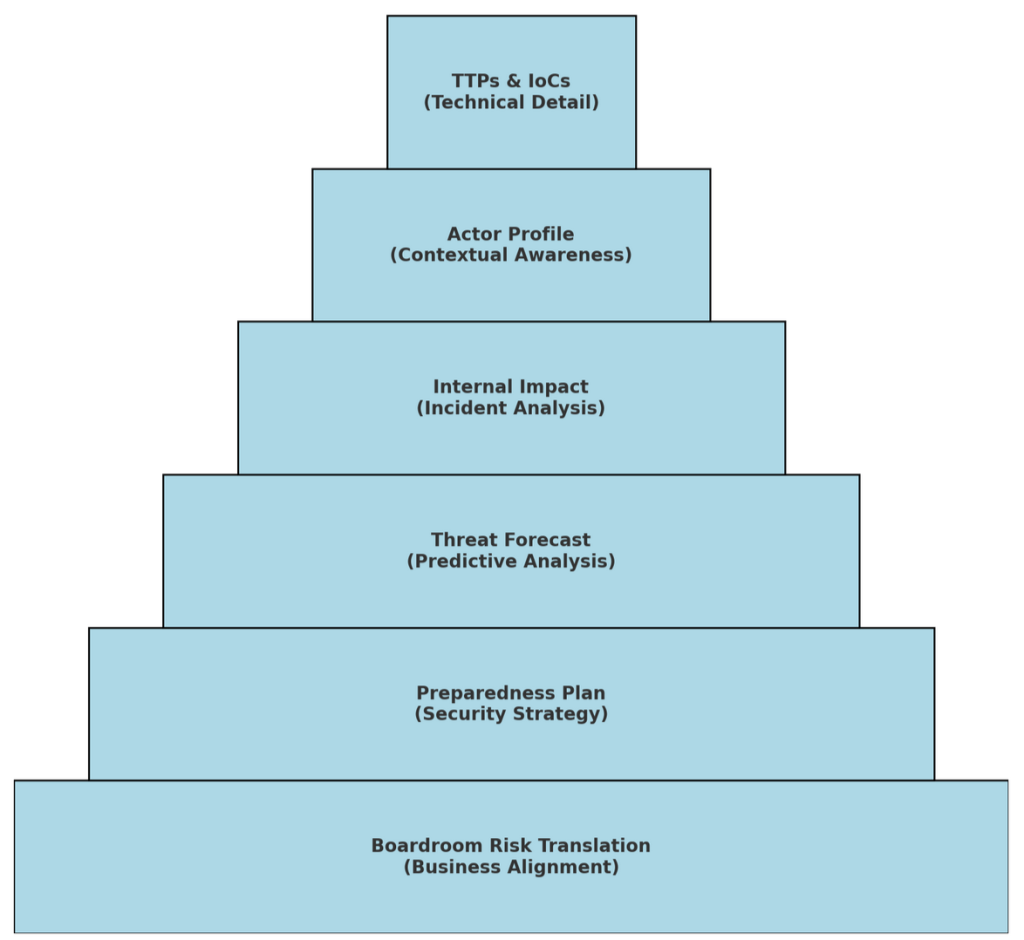
INTELscope Pyramid
- TTPs & IoCs – Technical signals from logs, endpoints
- Threat Actor Profile – Context from external sources
- Internal Impact – What they did in your environment
- Threat Forecasting – What they’re likely to do next
- Preparedness Plan – Your layered defense strategy
- Boardroom Risk Translation – Aligning with business objectives
Next blog: We’ll unpack each layer in detail and show how to make it work in your org.
Chip’s 3-Tiered Threat Actor Strategy
Want to focus your team’s energy? Here’s how Chip breaks it down:

| Tier | What It Means |
|---|---|
| Primary | They’ve already targeted you. Your logs, alerts, or reports confirm their presence. |
| Secondary | They’ve hit your partners, vendors, or subsidiaries. You may be in their wider scope. |
| Tertiary | They’re active in your sector or region. Not yet knocking, but possibly scouting. |
Start with primary. Stay alert on tertiary.
Special Note: For Teams Just Starting Out
New to threat actor profiling? No shame in the game. Start here:
- Pick one threat actor relevant to your industry, based on vendor reports or threat bulletins or your own research.
- Build a one-page profile with their known tools, TTPs, motivations, and history.
- Map their behavior to your environment using MITRE ATT&CK and your existing detection stack.
- Write a mini response plan that outlines steps from detection to escalation.
- Review every quarter to account for new tactics and infrastructure changes.
For Threat Intel Analysts & SOC Teams
Checklist for the win:
- Monitor threat feeds and alerts from sources like AlienVault OTX and Recorded Future.
- Correlate IOCs and behaviors to known threat actors using tools like ATT&CK Navigator.
- Tag indicators in your SIEM, so detection rules are tied to actors.
- Update playbooks regularly, ensuring they’re aligned with emerging campaigns.
- Feed insights into threat modeling sessions, tabletop exercises, and board-level reporting.
This is where intelligence becomes muscle memory.
Final Thoughts
Understanding “Who did it?” isn’t about finger-pointing. It’s about knowing the enemy, anticipating their moves, and turning threat intelligence into a business asset.
Stay tuned for the next blog—we’re going full pyramid mode.
Until then, stay sharp, stay curious, and remember: not all attackers wear hoodies, but all of them hate a well-prepared SOC.
Useful Tools for Threat Actor Profiling
- MITRE ATT&CK — Comprehensive framework of adversary tactics and techniques
- TheHive Project — Open source threat intel and response platform
- Sigma Rules — Generic signatures for SIEM systems
- ATT&CK Navigator — Visualization tool for ATT&CK mappings
- AlienVault OTX — Crowd-sourced threat intel platform
- MISP — Threat intelligence sharing platform
#ThreatIntel #CyberSecurity #SOCops #KnowYourEnemy







Leave a reply to Week 13 – 2025 – This Week In 4n6 Cancel reply