A Telegram post. A provocation. And a reminder that loyalty is still our most fragile control.
The Moment That Sparked This
It began with a Telegram post sliding through telegram chats late one Friday night.
“Our war is only with Australia. Not the Americans, not the British, not anyone else.
If you work at any major firm here – or even have access – message us.”
No ransomware, no exploit dump just words. Yet those words hit harder than malware: they made people look at each other differently. One sentence capable of making an entire workforce think, Who among us would reply?
For me the post felt like it was a loyalty test disguised as a headline, which let me dig a bit deeper on the story and context behind it.
So Why I’m Writing This
Because that message wasn’t an attack on systems; it was kind of social experiment on people (like we see people posting on their youtube channel). It proved how a few lines of text can turn human characteristics such as exhaustion, bad experience at workplace into opportunity for an adversary. We keep saying zero trust, but we rarely extend it to our own assumptions about people.
And that disconnect between technical control and human reality is what this article tries to bridge.
The Oldest Tradecraft in a New Uniform
We all know the saying “loose lips sinks ships”. Before malware, there were favours. Before phishing, there were promises. The mechanics evolved, encrypted chatrooms, crypto wallets, anonymity at scale but the intent never changed.
Groups like Lapsus$, ShinyHunters, and Scattered Spider didn’t invent this technique or method; they are just using the tools that directly exploits the most vulnerable link – We the people. In other words, they exploit a simple truth: in a tired workforce, trust becomes negotiable.They don’t hack systems; they hack sentiment.
Which leads to the question every defender eventually faces. How do we fight an attack that targets belief, not bandwidth?
Decoding the Event
Every blog or let’s say case begins with structured curiosity. My 5W model controls my curiosity long enough for intelligence to form and once the noise settles, the next question writes itself: So what do we do now?
| 5W | Insight |
|---|---|
| What Happened | Threat crews publicly invited Australians with corporate access to sell or share credentials. |
| Why It Happened | They exploit job insecurity and fatigue. Let’s call them human zero-days. |
| Why It Happened That Way | Public recruitment normalises betrayal and tests unity. |
| Who’s Involved | Lapsus$, ShinyHunters, Scattered Spider |
| What We Should Do | Build insider-risk playbooks blending detection, HR alignment, and psychological safety. |
The analysis gives us clarity let’s move to some actions.
The Playbook
Once the pattern is clear, defence becomes design. This is how we turn insight into motion.
- Disarm the Narrative Before you chase a suspect, neutralise the story. Every insider campaign begins with a myth such as “your company doesn’t care.” Counter it with truth before rumours harden into reason.
- Re-Route Fear into Reporting Fear can’t be deleted but it can be redirected. Make reporting feel like self-protection, not confession.
- Engineer Belonging You can’t policy your way out of apathy. Loyalty is infrastructure maintain it like uptime.
- Audit Access and Emotion If access reviews are quarterly, emotional reviews should be too. Pair privilege checks with well being checks; security plus HR equals situational awareness. Show empathy. Local or overseas employees are all valuable.
- End with Dignity, Not Dismissal Every exit interview is a containment control. Handle departures with respect; resentment has a half-life.
Takeaway Mindset
- Leadership is the real insider-threat control.
- Communication beats containment.
- Transparency travels faster than rumour.
- Culture isn’t a soft control, it’s a pre-incident response.
- Every disengaged employee is a pending security ticket.
Playbooks show what to do but what about those who can’t yet run them?
Broader Considerations for Organisations
Not every company can operationalise a full insider-risk playbook, but every company can build awareness. Cyber Awareness Month is the perfect moment to turn intelligence into culture.
Turn Intel into Awareness
Use the same event as a teaching moment. Show the Telegram post (sanitised), explain how such recruitment works, and remind staff where to report it. It’s still threat intelligence just told through storytelling instead of spreadsheets.
Fuse Functions Lightly
Even a single monthly check-in between SOC, HR, and Comms can prevent blind spots. You don’t need a fusion centre; you need shared context.
Lead with Visibility
When executives talk about loyalty as a security control, it reframes trust as part of defence posture. People protect what they feel part of.
And those small acts of coordination are what feed the next layer where every story becomes data and every data point becomes guidance.
From Playbook to Platform — The Thirdeye Intel Framework (Beta)
Each feeds into the upcoming Thirdeye Intel Framework, a living dataset that maps real stories to measurable controls. It’s not a static library; it’s an interactive beta launching in 2025 built to connect human narratives with NIST and MITRE functions.
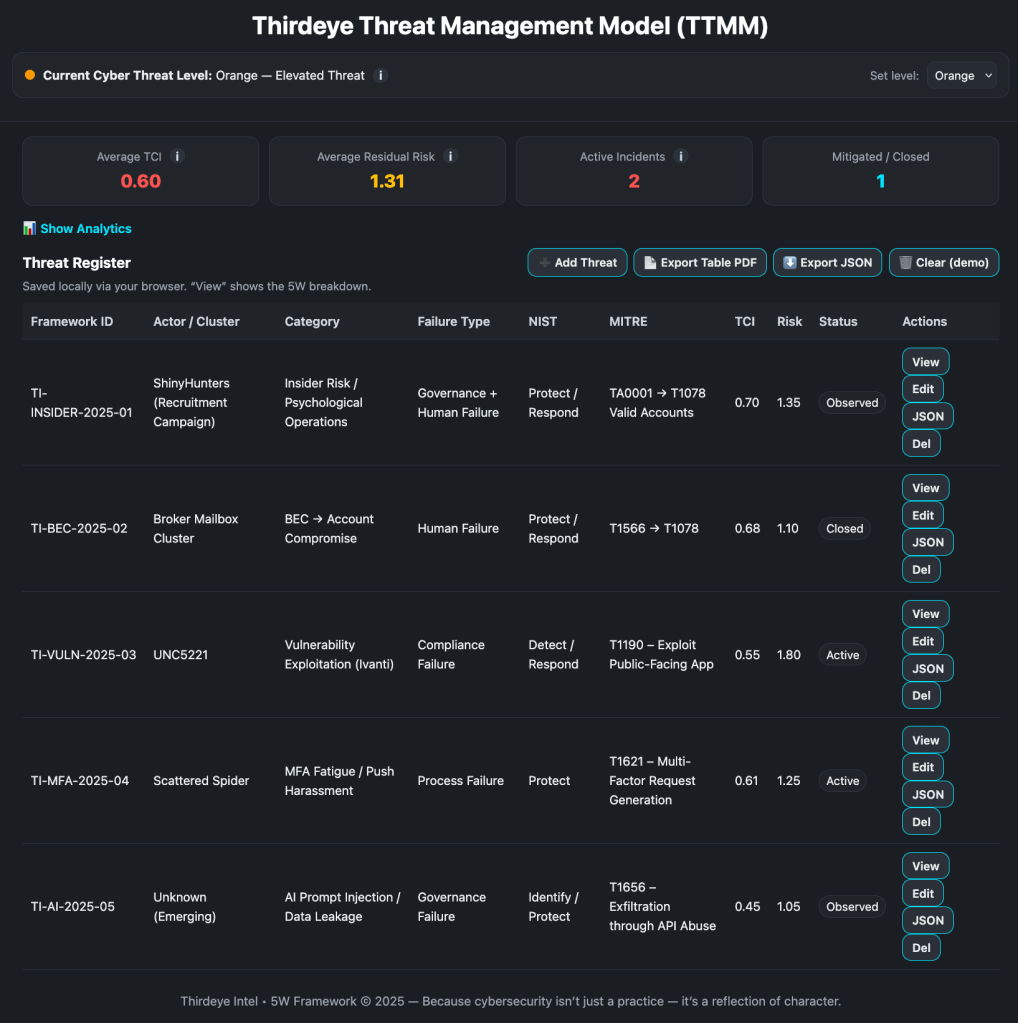
Metrics explain what happened; stories remind us why it mattered. Let’s close where it began with people.
Why It Matters
- No SIEM alerts on loneliness.
- No SOAR quarantines resentment.
- Those are the vulnerabilities being exploited now.
When someone says, “Our war is only with Australia,” they’re not testing our firewalls they’re testing our unity. Passing that test quietly, through care and clarity, may be the most patriotic act in cybersecurity.
Final Note
If you’d like to exchange insights or discuss active trends, connect with me on LinkedIn I’m always open to meaningful conversations about defence, culture, and strategy.
✍️ Because cybersecurity isn’t just a practice — it’s a reflection of character.







Leave a comment