Blog originally published on Medium – Jan 18, 2025

When was the last time your organization made a business decision without understanding the risks? I am sure many times and hope not anymore. But let’s be honest — how often does your security team’s involved in it. Many times they operate in isolation, solving yesterday’s problems while today’s threats pile up? In my opinion and experience, this is where the fusion center approach steps in, and trust me, it’s not just another buzzword.
Picture this: All threat intelligence teams should be considered a high-powered CPU, capable of processing endless streams of data from cybersecurity, fraud, and even physical security. At the end they rely on information.
A fusion center connects these threads, not just to keep your systems secure but to guide smarter business decisions. I implemented this approach at one my past organisation that I worked for, where risks like fraud, brand damage, and cyberattacks aren’t just threats — they’re are according to be business killers.
As mentioned in my last blog article, allow me to walk you through how this works and why it’s worth every ounce of effort.
Firstly, What is Fusion Center
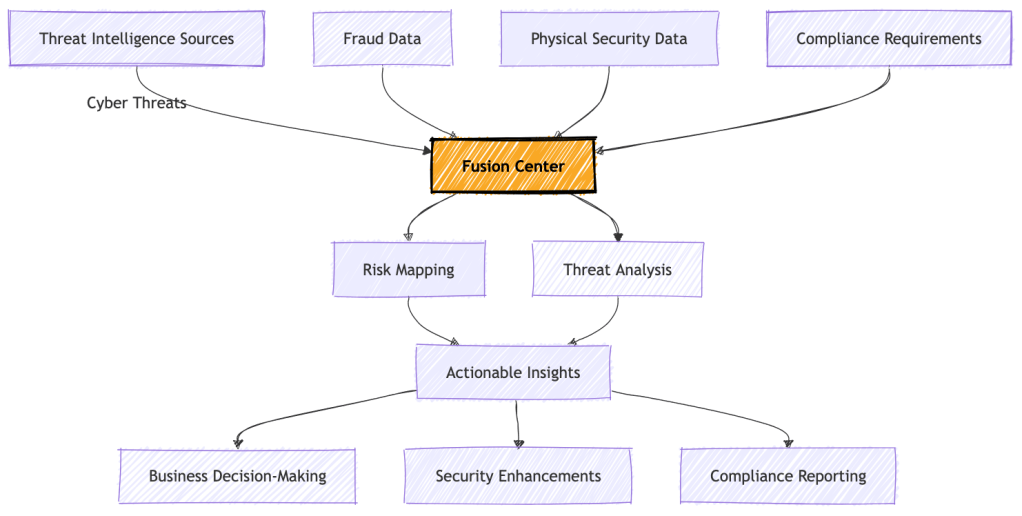
At its core, a fusion center is a centralised hub designed to collect, analyze, and disseminate intelligence from various domains — cybersecurity, fraud, physical security, and business continuity. It ensures that organisations operate with a unified, intelligence-driven strategy to reduce risks and bolster resilience.
My implementation in my past role sector was inspired and rooted in an intelligence-led approach, where threat intelligence played the role of a high-powered CPU, centralising critical insights to guide security measures and business decisions.
Why a Fusion Center?
A fusion center isn’t a fancy name for another silo; it’s a bridge. Its job is to centralise intelligence, break down barriers between teams, and ensure everyone is focused on what matters most — understanding risks, anticipating threats, and taking action before the damage is done.
Here’s how I broke it down:
- Start with intelligence: What are the biggest threats to your business?
- Connect the dots: How do these threats feed into risks like fraud, compliance failures, or reputational damage?
- Take action: What can the business do today to mitigate those risks tomorrow?
Taking example of financial services, this is essential. Think about the interconnected risks: a cyberattack that leads to fraud, which damages trust in your brand and hits your bottom line. Without a fusion center approach, those dots often remain unconnected — until it’s too late.
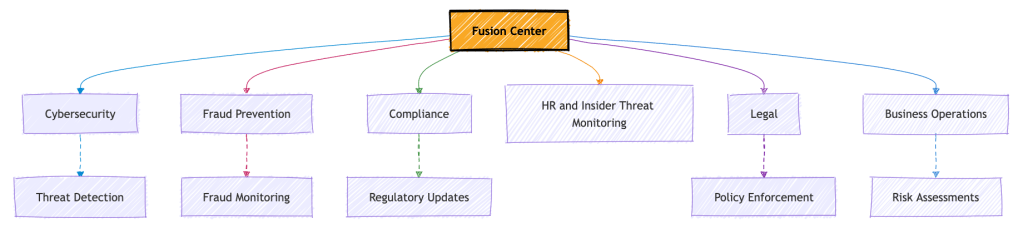
Key Components of a Fusion Center
Structure Overview
The diagram below illustrates how a fusion center integrates various departments, making it a collaborative hub:
So let’s understand how one can establish a fusion center. NOTE: The approach should be customised based on your organisation requirements and objectives.
How to Establish a Fusion Center
Step 1: Start with People
A fusion center thrives on collaboration, so assembling the right team is critical. Here’s what you need:
- Key Individuals:
- Subject Matter Experts (SMEs): Specialists from your cybersecurity, fraud prevention, compliance, physical security, and business operations teams. One add more depending on how the organisation is spanned.
- Decision Makers: Senior management and/or executive leadership who can prioritize risks and allocate resources effectively.
- Roles to Include:
- Threat Intelligence Analysts: The brains behind intelligence collection and analysis.
- Incident Response Leads: Experts who coordinate responses to active threats.
- Fraud Prevention Specialists: Focus on detecting and mitigating fraud-related risks.
- Compliance team: Ensure alignment with regulations like CPS230, ISO 27001, and CPS234.
- External Liaisons: Internal teams who manage communication with law enforcement, peer institutions, and external stakeholders.
Tip: Look for team members who are not only skilled in their domain but also excel in communication and teamwork. A fusion center thrives on breaking silos, and that starts with the people.
Step 2: Choose a Physical or Virtual Location
While physical fusion centers offer a centralized space for teams to collaborate, many organizations are opting for hybrid or virtual setups.
- Physical Location Benefits:
- Facilitates real-time collaboration during crises.
- Builds stronger team rapport through in-person meetings.
- Virtual Setup:
- Reduces costs and enables access to global team and in different timezone.
- Leverages collaboration tools like secure video conferencing, shared dashboards, and threat intelligence platforms.
Tip: Do consider prioritising regular in-person meetings to strengthen team dynamics and decision-making. A quarterly in-person session can make a big difference.
Step 3: Establish Processes and Governance
A fusion center is only as good as the processes that guide it. Here’s what to set up:
- Information Flow:
- Define how intelligence is collected, analyzed, and shared across teams.
- Use tools like threat intelligence platforms to centralize data if available.
- Clear Objectives:
- Focus on intelligence-led outcomes, like identifying business-critical risks and actionable threats.
- Align processes with compliance goals, such as CPS230’s operational resilience requirements.
- Decision-Making Framework:
- Define who makes the call during incidents (e.g., fraud detected, regulatory breach).
- Empower SMEs and decision-makers to act quickly and decisively.
- Incident Response Playbooks:
- Create standardized workflows for responding to various threats (cyberattacks, fraud, physical risks).
Step 4: Implement Technology to Support Collaboration
The right tools amplify the fusion center’s effectiveness. Invest in:
- Threat Intelligence Platforms: Centralize data collection and analysis.
- Collaboration Tools: Secure chat, video conferencing, and document-sharing platforms.
- Analytics Tools: For fraud detection, threat modeling, and compliance tracking.
- Automation: Use AI to detect anomalies and automate repetitive tasks like log analysis.
Step 5: Build a Culture of Collaboration
Establishing a fusion center isn’t just a structural shift; it’s a cultural one.
- Encourage cross-departmental communication through shared goals and frequent updates.
- Foster a mindset where security is everyone’s responsibility.
- Celebrate successes — whether it’s detecting a fraud attempt or improving response times — to keep morale high.
Step 6: Define Metrics for Success
You can’t manage what you don’t measure. Track these key metrics to evaluate your fusion center’s performance:
- Incident Response Time: How quickly does the team detect, analyze, and mitigate threats?
- Fraud Prevention Rate: The percentage of fraud attempts detected and blocked.
- Threat Intelligence Usage: How often shared intelligence influences decisions.
- Compliance Outcomes: Fewer regulatory violations and improved audit results.
Case Study: Preventing Payment Fraud — A Fusion Center in Action
Around and beyond 2015, Australian financial organisations began noticing increase in unauthorised transactions, with multiple financial institution realized it was under attack. The culprit? The infamous Gozi malware, a sophisticated threat that wreaked havoc across banking systems worldwide. Note, there were other banking malware families (Trickbot, Marcher, Zbot etc), and similar approach was taken however, this one particularly had significant mark to the business.
Gozi doesn’t just steal credentials; it injects itself into user devices, stealthily monitors banking sessions, and siphons off funds via money mule networks. This case highlights how the fusion center approach, blending intelligence, collaboration, and external outreach, mitigated a significant threat and protected both customers and the organisation.
The Threat: Gozi Malware
Gozi targeted customers with phishing emails designed to look like legitimate communications from the bank. When a victim clicked on the link, the malware installed itself on their device, hijacked their banking sessions, and stole login credentials. The malware’s ultimate goal was to transfer funds into accounts controlled by money mules, who would then funnel the stolen money further.
The Fusion Center’s Response
Threat Intelligence Analysis:
As part of the fusion center’s threat intelligence team, we simulated the Gozi malware in our lab to understand its behavior:
- Key Indicators Identified: We pinpointed specific changes Gozi made during banking sessions, including unique network traffic patterns, unauthorised script injections, and anomalous session behaviors.
- Detection Opportunities: This intelligence enabled the development of detection signatures tailored to recognize Gozi’s activity.
Collaboration with the Fraud Team:
We shared the malware indicators with the fraud prevention team, enabling them to:
- Monitor Transactions: Identify suspicious activities, such as unexpected fund transfers to flagged mule accounts.
- Flag Compromised Accounts: Notify impacted customers and temporarily freeze their accounts to prevent further losses.
External Communication and Intelligence Sharing:
The fusion center didn’t stop at internal response:
- Assisting the Banking Community: Intelligence on Gozi’s behavior and indicators was shared with other financial institutions via industry partnerships. This proactive communication helped prevent similar attacks across the sector.
- Collaboration with Law Enforcement: When money mule networks were identified, the fusion center coordinated with law enforcement to disrupt their operations, leading to arrests and recovery of stolen funds.
Business benefits of Fusion Centers
The fusion center’s coordinated response brought several critical benefits to the business:
- Reduced Fraud Losses: By detecting and blocking Gozi-related activities early, the bank saved millions in potential fraud losses.
- Improved Customer Trust: The proactive identification and resolution of threats reassured customers that the institution was actively safeguarding their assets, bolstering loyalty and brand reputation.
- Enhanced Industry Standing: Sharing threat intelligence with peers showcased the bank’s leadership in the financial sector and contributed to industry-wide resilience.
- Regulatory Compliance: By coordinating with law enforcement and maintaining detailed documentation, the bank demonstrated compliance with frameworks like CPS230 and ISO 27001, which emphasize operational resilience and proactive risk management.
- Faster Response Times: The fusion center’s centralized structure eliminated silos, enabling faster decision-making and response times during the attack.
Conclusion
This case is a prime example of how a fusion center acts as the nervous system of a security strategy. It ensures that:
- Intelligence is centralized and actionable.
- Collaboration bridges the gap between cybersecurity, fraud, and external partners.
- Responses are coordinated to mitigate risks efficiently.
Thanks to the fusion center, the organization didn’t just defend against Gozi — it turned the threat into an opportunity to strengthen its security posture, enhance customer trust, and contribute to the financial sector’s collective defense.
Takeaway: The fusion center isn’t just a security investment; it’s a business enabler, protecting assets while driving trust and resilience across the board.
Thanks all. Stay Safe Stay vigilant!!







Leave a comment